Although a number of new ways of communicating have been launched in recent years, e-mail is still the most common way of communicating digitally. In various surveys around the world, more than 90% of those surveyed state that they prefer e-mail as the main communication channel.

At the same time, it can be stated that the security and anonymity of e-mails is still downright lousy. Even though the major players are gradually introducing various types of increased security, the absolute majority of sent e-mails are in principle completely unprotected.
The reasons for this are partly a complex and often expensive technology behind the protection that many find difficult to absorb, and partly it is a matter of money.
Companies and organizations that have the greatest need and are the most driving at the same time account for only about 25% of e-mail accounts, which affects the development of both good and evil. The technical development is driven forward. But for one, especially for smaller organizations and private individuals, too high a cost.
Something that further complicates the whole thing is the ever-increasing regulatory requirements that not only to protect privacy and other things through eg GDPR and the like, but also that the authorities should have access to e-mail “when needed”.
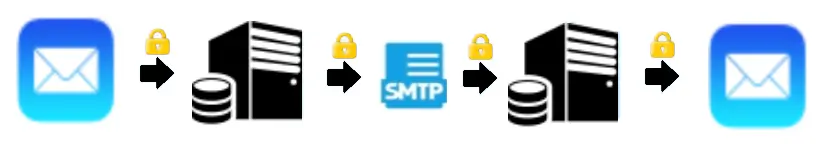
A completely secure system uses End-To-End encryption where the e-mail message (including attachments) is encrypted in the sending e-mail client and decrypted in the receiving e-mail client. The message, even if it is encrypted, must also be transported and stored securely.
The disadvantage of this solution is that all messages are always encrypted in the systems and therefore difficult to make searchable or administer in different ways. It is usually also impossible to decrypt all messages if, for example, the encryption keys are lost.
It is therefore becoming increasingly common to use two parallel e-mail systems; one with high security but without E2EE for the standard email (@ mindomain.com), and an E2EE system on a subdomain (@ secure.mindomain.com) for the group in the organization that needs extra sensitive communication.

Some solutions, such as ProtonMail that we work with, use a proxy installed locally in your own computer between ProtonMail’s email system and the local email client. The proxy handles encryption and decryption and the regular e-mail client, eg MS Outlook, can thus handle sensitive e-mail in the same way as other e-mail without tricky extra measures.

It is also possible to combine E2EE e-mail with secure and anonymised web forms. Something that is required, for example, in the new “whistleblower directive” which affects all companies with more than 50 employees or municipalities with 10,000 or more inhabitants. The message is already encrypted in the web form in the browser and then sent via the E2EE e-mail system.
All companies and organizations should use E2EE email and web forms as a complement to succeed in meeting today’s requirements for privacy and even anonymity. The solutions we offer are neither difficult nor expensive.