Who should have the right, or even the opportunity, to read your emails? The obvious answer should be; I who send and you who receive the message.

In reality, it does not work that way at all. In fact, there are quite a few who have access to your digital communications; everything from the staff who take care of the systems that handle your messages, to cybercriminals who break in or steal on the road, to authorities who, under various pretexts, request access.
And when a message is sent, data is created and saved in the form of cache, intermediate storage, various logs, metadata, etc. In some cases, for example, your message can be saved complete with not only the content in clear text, but also info about sender, recipient, time and a lot of other sensitive data, in a forgotten server log somewhere.
This also applies to all web forms that use e-mail as transport, something that is often forgotten in these contexts. When we mention “e-mail client” in this article, we also include the web forms that are sent via e-mail.
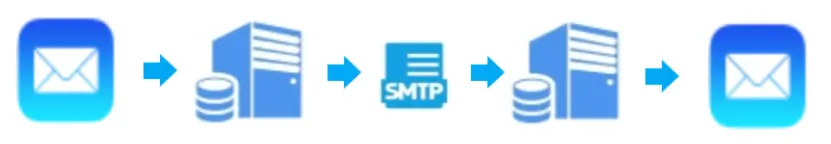
“Regular e-mail” is always sent in full text via insecure transport routes. Some e-mail servers and e-mail clients create encrypted tunnels for the actual transport, others do not. Everything is saved in clear text in the e-mail boxes, everything is logged and is traceable, often entire messages in clear text can end up in, for example, error logs. Security and anonymity are virtually non-existent.
An important first step in protecting e-mail messages is to require the creation of secure transport between sender and recipient via an encrypted tunnel (SSH/TLS). The message is still sent and saved in clear text and creates a trace but is protected from being stolen during the actual transport (MITM, Man-In-The-Middle attacks) between the clients and the server systems.
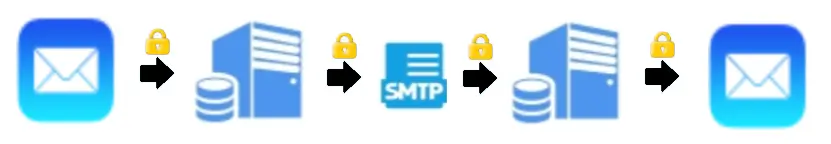
The next important step is to also protect the server systems by encrypting hard disks and databases as protection against data loss through, for example, burglary or theft of hardware.
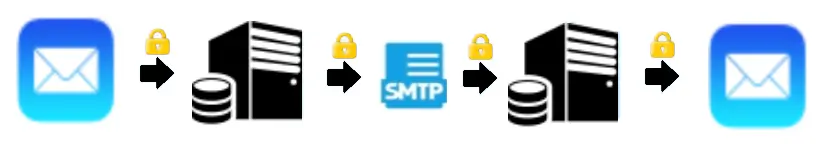
In the third step, which is becoming more common, the message itself is also encrypted when it is transported between servers and when it is saved in the server system. This is often marketed as a secure encryption system but it is important to note that the message can still be read by the systems and anyone who has access to them.
If an encrypted e-mail is sent to someone who does not have the function, the recipient receives an e-mail with a link to a web-based e-mail client where the encrypted message can be read and often also replied to.
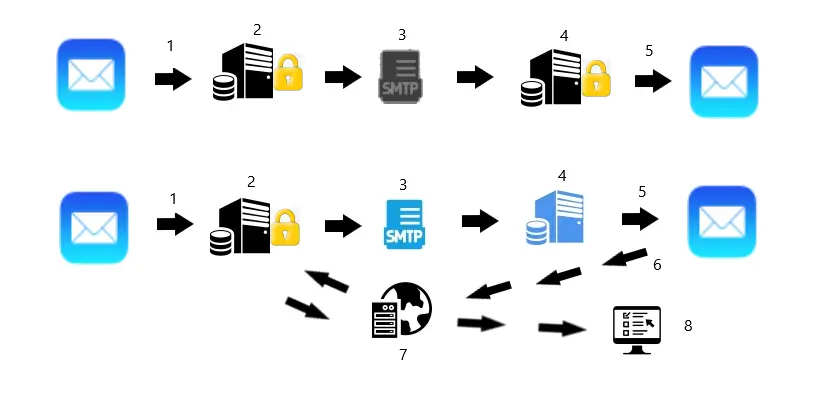
In a fourth step on the security ladder, the e-mail message is encrypted/decrypted in the e-mail client, so-called E2EE (End-to-end encryption), and can thus not be read by unauthorized persons in any context. Otherwise, most things work as in step three, but with the difference that the message is and remains encrypted during the entire transport and when it is archived.

Anonymity is also very important in these contexts but often completely overlooked. In addition to the e-mail itself, a lot of information about the message is created in different caches, in cookies, as metadata and not least in different logs. This happens in all parts of the chain; on the client computer, in the client’s browser and in all server systems that somehow handle the message. With the right tools and knowledge, in fact, most e-mails, also “secure” ones, can be tracked all the way and sometimes even completely reconstructed.
You, who in some way handle sensitive information and need to communicate via e-mail and web forms therefore need anonymized E2EE for your communication.